| |
| Windows Password Recovery Tools & Techniques |
|
|
|
|
|
|
|
| |
| |
|
| |
|
In this article we will discuss various ways through which user
can recover or reset his current as well as remote windows password.
Sometimes it is more easy to reset the windows password than actually
recover the password provided user has access to physical system.
Often its more important recover the password especially when file
system is encrypted or when file system is analyzed for Forensic cases.

Windows 98 used to store the user account passwords in .pwl files
in Windows directory. Later version of Windows more better technique
and stores the account password into registry hive files named
'SYSTEM' and 'SAM' at following location
|
|
| C:\Windows\System32\Config |
|
| These files are highly protected and not accessible while Windows is
running even for the administrator user. However hackers have found a
way to circumvent these protections and access these system files. |
|
|
|
|
|
This section deals with recovering all user account passwords
from currently logged in system. In addition to the currently logged
on user, you can also recover passwords of all other user accounts
on the same system. For this you need to have an account with
administrative privileges.
There are couple of tools available for live windows password
recovery such as pwdump, cain & abel, LC5 etc. Entire process
involves 2 steps
|
- Dumping the LM/NTLM password hashes of target user
account
- Recovering the password using
RainbowCrack/BruteForce/DictionaryCrack method.
|
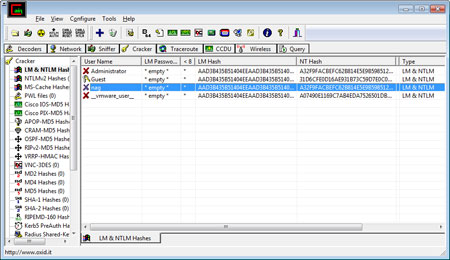
| Here is the snapshot of various user
accounts and their LM/NTLM hashes dumped by
Cain & Abel tool [2] |
| |
 |
| |
It will dump the password hashes (LM/NTLM) for all
the user accounts and mention if any of the user account don't have
any password. After getting these hashes, you can submit it to
online rainbow cracking services to quickly recover real password.
For more details refer to our 'Rainbow Password Cracking Article'.
You can also give it try using Windows Password Kracker tool to recover the dictionary based passwords. |
| |
|
This section is throw light on how we can recover the password from
offline system or just plain hard disk. Generally this is the case with
Forensic investigations where in person's disk has been brought in for
acquiring further foot prints in the case. In such scenarios it is
important to recover the user's login password as the disk may have been
encrypted and some of the prominent applications uses user's logon
password to secure their data and other credentials.
Here we will discuss both scenarios, resetting the current user
password as well as recovering the password from offline system or hard
disk.
|
| |
| |
|
|
Here we are going to use chntpw tool from
BackTrack live CD. Here are
the typical steps involved in resetting the password |
- Connect your target Hard disk whose accounts needs to be reset
to the running system.
- Boot the system using BackTrack live CD.
- AAfter login, unmount the target hard disk and remount it in
read/write mode using following commands
- umount /mnt/hda1
- modprobe fuse
- ntfsmount /dev/hda1 /mnt/hda1
- mount
- Next launch the chntpw tool from the \Windows\System32\Config
folder passing 'SAM' file as parameter as shown below
- /mnt/hda1/Windows/System32/Config > chntpw SAM
- Chntpw will display all users and you are asked to select
particular user to reset the password.
- On selecting the user, you can choose option to reset the
password, where you can enter '*' to set the password to blank.
After that you can save the changes and quit the tool.
- Finally unmount the drives and restart the system from hard
disk. Now you can login to the system with that user and blank
password.
|
| |
| This technique can discover any userland Rootkit process and only
way for rootkit process to defeat against this technique is to move into
kernel. However, due to low-level implementation, there is slight risk
in using this method in production code. |
| |
| |
|
Offline recovery involves copying
SYSTEM and SAM registry hive files from target system. You can
use any of the LIVE CD or other mechanism to access the Hard
disk and get the files.
Here we will explain how we can get
those files using BackTrack Live CD
. |
- Make sure that target hard disk is connected to
the system.
- Now boot the system using BackTrack Live cd.
- By defaults target hard disk file system is
mounted on to /mnt/hda1 (or /mnt/sda1). You can check
the mount points using the 'mount' command.
- Then move on to following folder and copy SYSTEM
& SAM files to USB or any other media.
- /mnt/hda1/Windows/System32/Config
- Once these files are copied, you can use emote
system password recovery wizard of either LC5 or
'Cain &
Abel' tool to dump the hashes by passing these files.
- Once password hashes are obtained, next task is
to use
Rainbow cracking service or Dictionary/BruteForce operation to recover
the password as mentioned earlier.
|
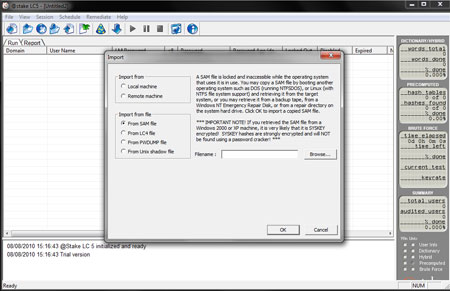
| Here is the screenshot of recovering the password from SAM file
using the LC5 tool. |
| |
 |
| |
| |
|
In case you have forgotten password to your Windows box and just
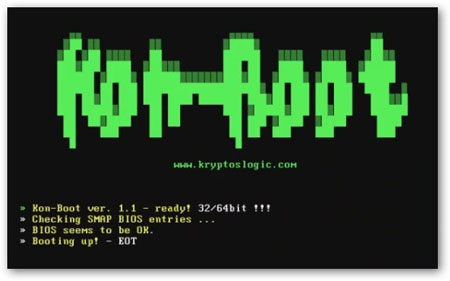
want to login without doing any recovery or reset then
Kon-Boot will help you
get into any Windows box (and some Linux boxes too) without any
password.
Kon-Boot is an prototype piece of software which allows you to
access any password protected Windows system without any knowledge of
the password. It dynamically modifies the Kernel memory to completely
bypass the default authentication mechanism leading to complete access
to any Windows box. |
| |
 |
| |
| Kon-Boot works supports all windows systems starting from Windows XP
to latest Windows 7. Newer version now supports both 32 bit & 64 bit platforms. This tool will be more useful for Forensic
investigators and law enforcement professionals. |
| |
| |
|
|
Often in the corporate environment, there is a need to remotely
troubleshoot user login problems, such as recovering or resetting the
password. Generally in such scenarios, every client system will have one
administrator account and one or more user accounts. Administrator can remotely recover the user passwords using the tools
like pwdump.
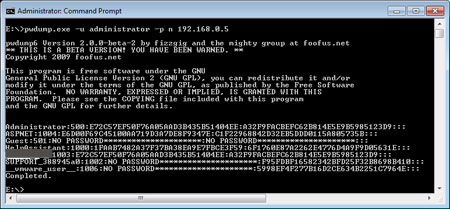
Pwdump is the great tool which can dump the password hashes not only
from live system but also from the remote system. Here is the
screenshot of pwdump dumping the password hashes for all account from
remote system.
|
|
|
 |
| |
|
Here pwdump prints it to the console, instead you can make it to write
to text file which can be later fed into LC5 or Cain & Abel or Windows Password Kracker for brute
force/Dictionary crack operation.
Alternatively you can submit the
hashes to online
Rainbow cracking service [5] to quickly recover the password. |
| |
| |
|
[1]. Tool: L0pthCrack
- LC5
[2]. Tool: Cain & Abel
[3]. Tool: Windows Password Kracker
[4]. Tool: Pwdump
- Windows Live & Remote Password Recovery Tool
[5]. BackTrack - Popular
Linux based Security Distribution
[6]. Rainbow Cracking to quickly recover Windows Password.
[7]. Kon-Boot: Boot CD to login to
Windows Box bypassing the Authentication |
| |
| |
|
|
|
|